Exploit — Bash Shellshock Part 1. In September 2014, when a single…, by ka1d0
Por um escritor misterioso
Last updated 17 maio 2024

In September 2014, when a single security bug in Bash was disclosed there was chaos in the security community. This bug allowed attackers to escalate privileges and execute arbitrary code on a remote…
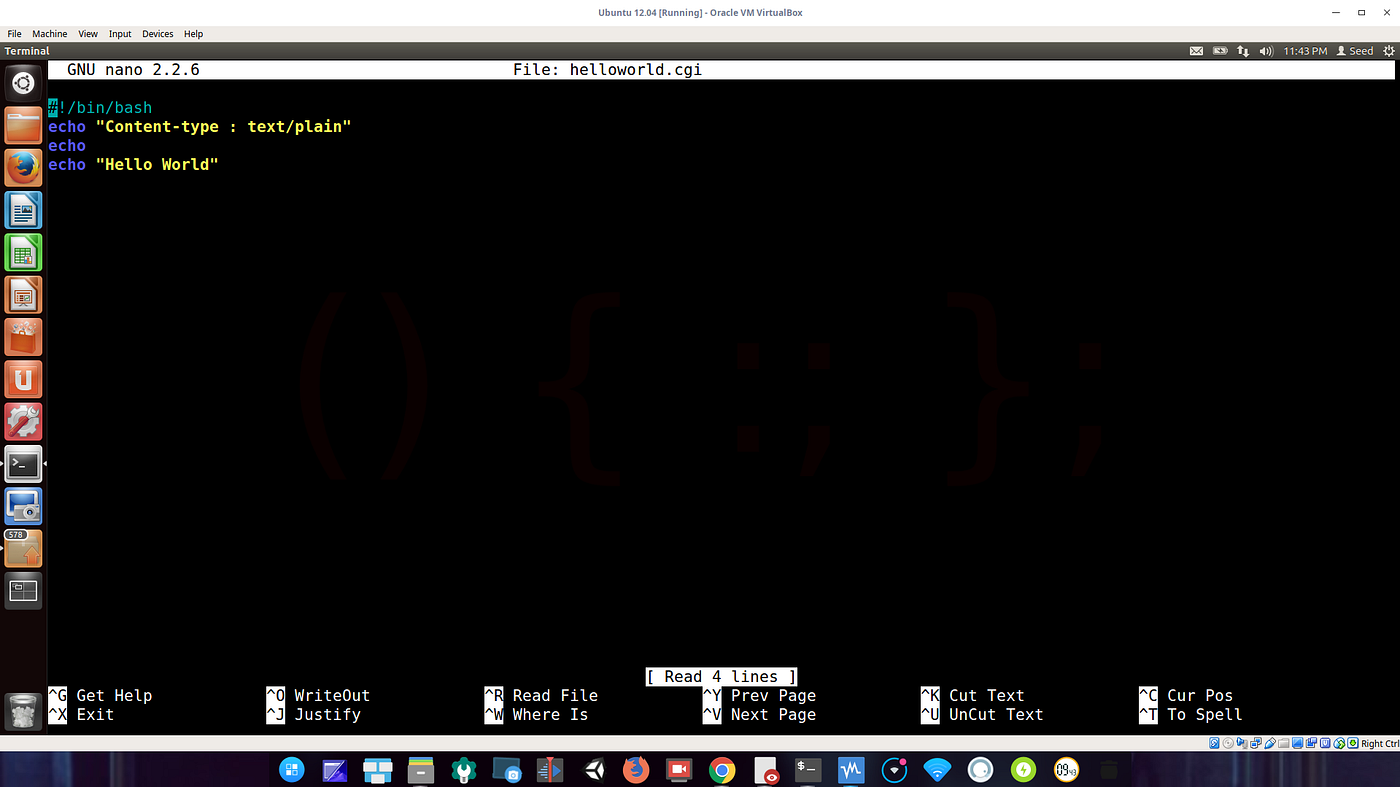
Shellshock Attack on a remote web server, by Anshuman Pattnaik
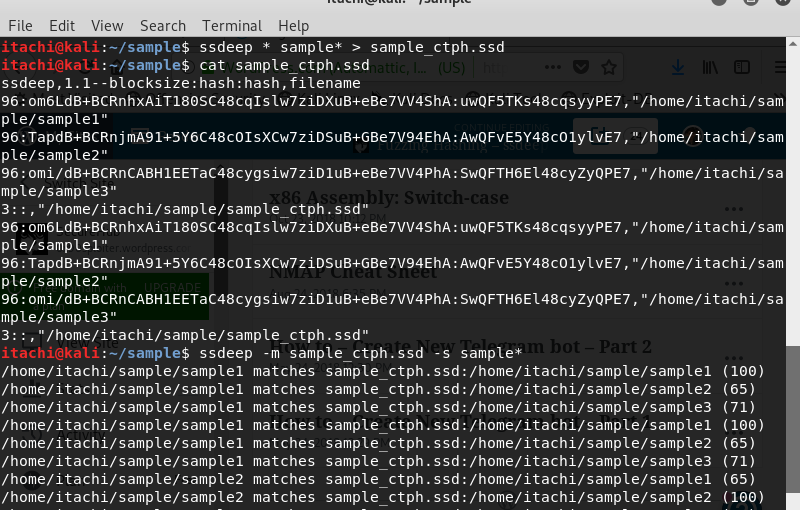
Threat Attribution using ssdeep. We have all used cryptographic hashes…, by ka1d0
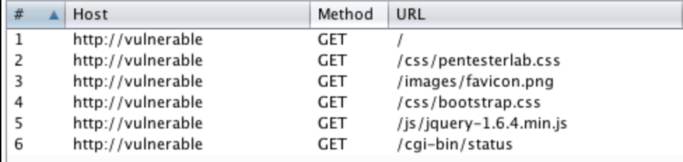
PentesterLab: Learn Web App Pentesting!
Bitcoin Blockchain as a Graph in Neo4j, by ka1d0

Shellshock Bash Vulnerability

ShellShock – Hands-On

Exploit — Bash Shellshock Part 1. In September 2014, when a single…, by ka1d0
Pentesting — VulnHub: DC-1. This post is one of the many that I'll…, by ka1d0
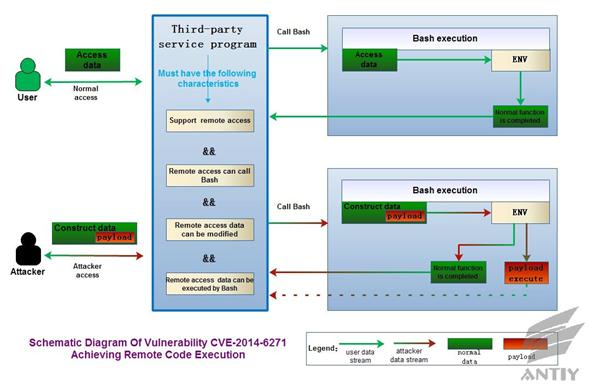
A Comprehensive Analysis on Bash Shellshock (CVE-2014-6271)_V1.53 ——Series One of Bash Shellshock Analysis - Antiy Labs
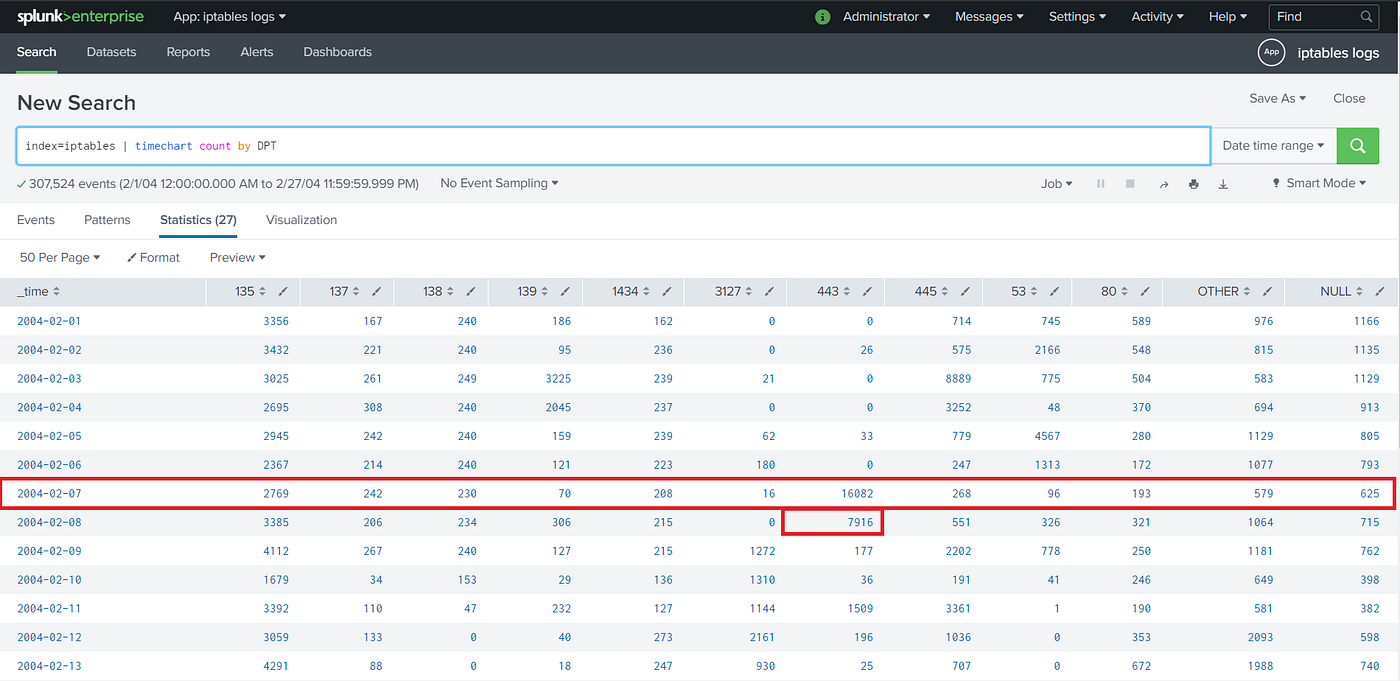
Writing Basic Splunk Rules. The 21st century is the age where…, by ka1d0
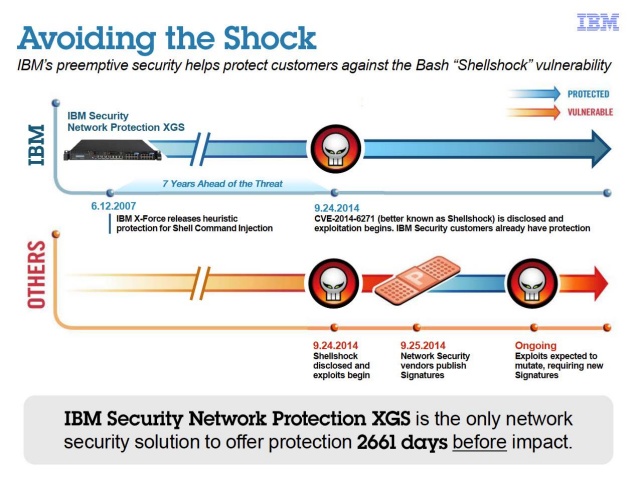
How Bash Shellshock Exploits Could've Been Avoided 7 Years Ago
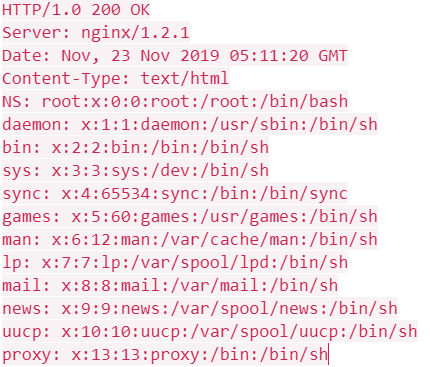
Shellshock Bash Remote Code Execution Vulnerability Explained - BreachLock
Recomendado para você
-
 A new BASHLITE variant infects devices running BusyBox17 maio 2024
A new BASHLITE variant infects devices running BusyBox17 maio 2024 -
 35 Shellshock Images, Stock Photos, 3D objects, & Vectors17 maio 2024
35 Shellshock Images, Stock Photos, 3D objects, & Vectors17 maio 2024 -
 Shellshock In-Depth: Why This Old Vulnerability Won't Go Away17 maio 2024
Shellshock In-Depth: Why This Old Vulnerability Won't Go Away17 maio 2024 -
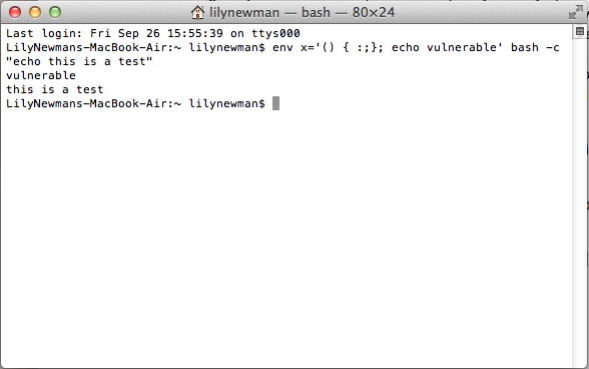 Shellshock: What you need to know about the Bash vulnerability.17 maio 2024
Shellshock: What you need to know about the Bash vulnerability.17 maio 2024 -
 Tenable Issues Shellshock Detection Plugins, Wizard, Dashboard - Blog17 maio 2024
Tenable Issues Shellshock Detection Plugins, Wizard, Dashboard - Blog17 maio 2024 -
 Worm exploits Shellshock to infect QNAP systems17 maio 2024
Worm exploits Shellshock to infect QNAP systems17 maio 2024 -
 Hunting For Shellshock Using Nessus17 maio 2024
Hunting For Shellshock Using Nessus17 maio 2024 -
 Hackers seize Apple computers as Shellshock cyber bug strikes17 maio 2024
Hackers seize Apple computers as Shellshock cyber bug strikes17 maio 2024 -
 Lab: Blind SSRF with Shellshock exploitation17 maio 2024
Lab: Blind SSRF with Shellshock exploitation17 maio 2024 -
![Outdated] Con's Shell Shock Live Aimbot [Source Code] - MPGH - MultiPlayer Game Hacking & Cheats](https://i.imgur.com/EZKbChh.png) Outdated] Con's Shell Shock Live Aimbot [Source Code] - MPGH - MultiPlayer Game Hacking & Cheats17 maio 2024
Outdated] Con's Shell Shock Live Aimbot [Source Code] - MPGH - MultiPlayer Game Hacking & Cheats17 maio 2024
você pode gostar
-
 Pokémon Meganium AMINO Chikorita Riolu, shiny gardevoir, png17 maio 2024
Pokémon Meganium AMINO Chikorita Riolu, shiny gardevoir, png17 maio 2024 -
 Team - Soccer, Football, Hockey, Basketball Club & eSport HTML Template by torbara17 maio 2024
Team - Soccer, Football, Hockey, Basketball Club & eSport HTML Template by torbara17 maio 2024 -
 NOVO CÓDIGO +TODOS OS 9 CÓDIGOS DE RESET STATUS DO BLOX FRUITS17 maio 2024
NOVO CÓDIGO +TODOS OS 9 CÓDIGOS DE RESET STATUS DO BLOX FRUITS17 maio 2024 -
 The Last Of Us 1 Remake PS5 MÍDIA DIGITAL - FireflyGames - BR17 maio 2024
The Last Of Us 1 Remake PS5 MÍDIA DIGITAL - FireflyGames - BR17 maio 2024 -
 La próxima película de Wataten! revela un nuevo avance — Kudasai17 maio 2024
La próxima película de Wataten! revela un nuevo avance — Kudasai17 maio 2024 -
 Crítica A Bruxa (The Witch, 2016) - Cine Eterno - Cinema Sem17 maio 2024
Crítica A Bruxa (The Witch, 2016) - Cine Eterno - Cinema Sem17 maio 2024 -
![2048x1152] - Techno / Cyberpunk City : wallpaper Cyberpunk city, Live screen wallpaper, Computer wallpaper hd](https://i.pinimg.com/originals/86/a5/7b/86a57bba7e94a6fca0d27c433b8239fc.jpg) 2048x1152] - Techno / Cyberpunk City : wallpaper Cyberpunk city, Live screen wallpaper, Computer wallpaper hd17 maio 2024
2048x1152] - Techno / Cyberpunk City : wallpaper Cyberpunk city, Live screen wallpaper, Computer wallpaper hd17 maio 2024 -
 Triciclo Infantil com Empurrador - Triciclo Baby City - Rosa17 maio 2024
Triciclo Infantil com Empurrador - Triciclo Baby City - Rosa17 maio 2024 -
Sakamoto Days Chapter 38 Discussion - Forums17 maio 2024
-
 Why Shazam! Fury Of The Gods Bombed At The Box Office17 maio 2024
Why Shazam! Fury Of The Gods Bombed At The Box Office17 maio 2024
